Introduction
Building Blocks
VeeaCloud
VeeaCloud, our comprehensive service suite, facilitates each phase of deployment, offering intuitive tools for configuration, management, and analytics. It ensures continuous application performance, even during public network disruptions, by balancing central and local orchestration.
VeeaWare
VeeaWare is the distributed software foundation vital to the Veea Edge Platform, designed to meet the complexities of edge computing. It facilitates a distributed processing model where multiple processing elements, spread across various locations, are managed and coordinated seamlessly.
Management & Monitoring
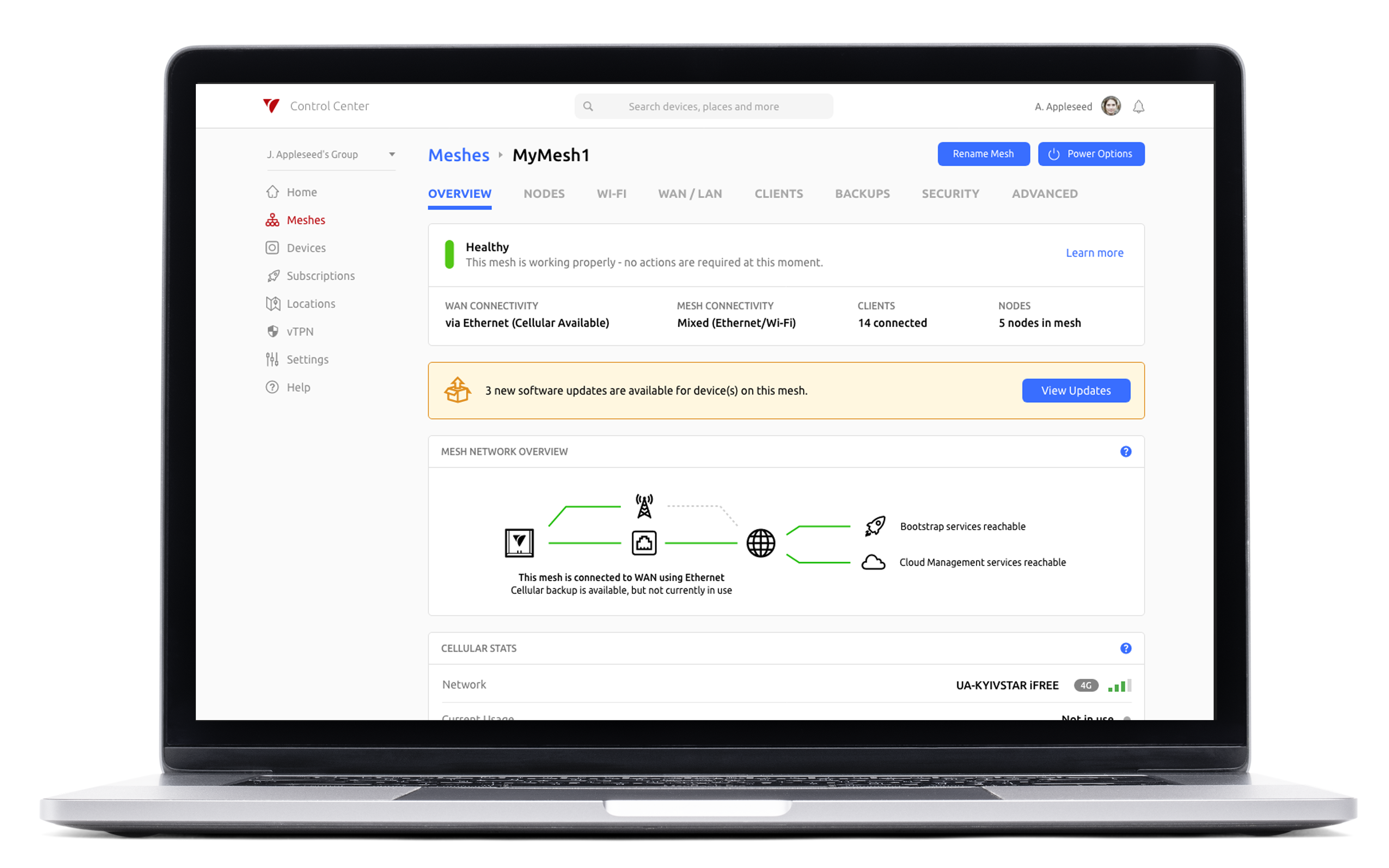
Control Center
A unified portal for effortless management of devices and applications. It allows for detailed oversight of VeeaHubs and mesh networks, complemented by in-depth analytics for improved system performance and cost-saving strategies.
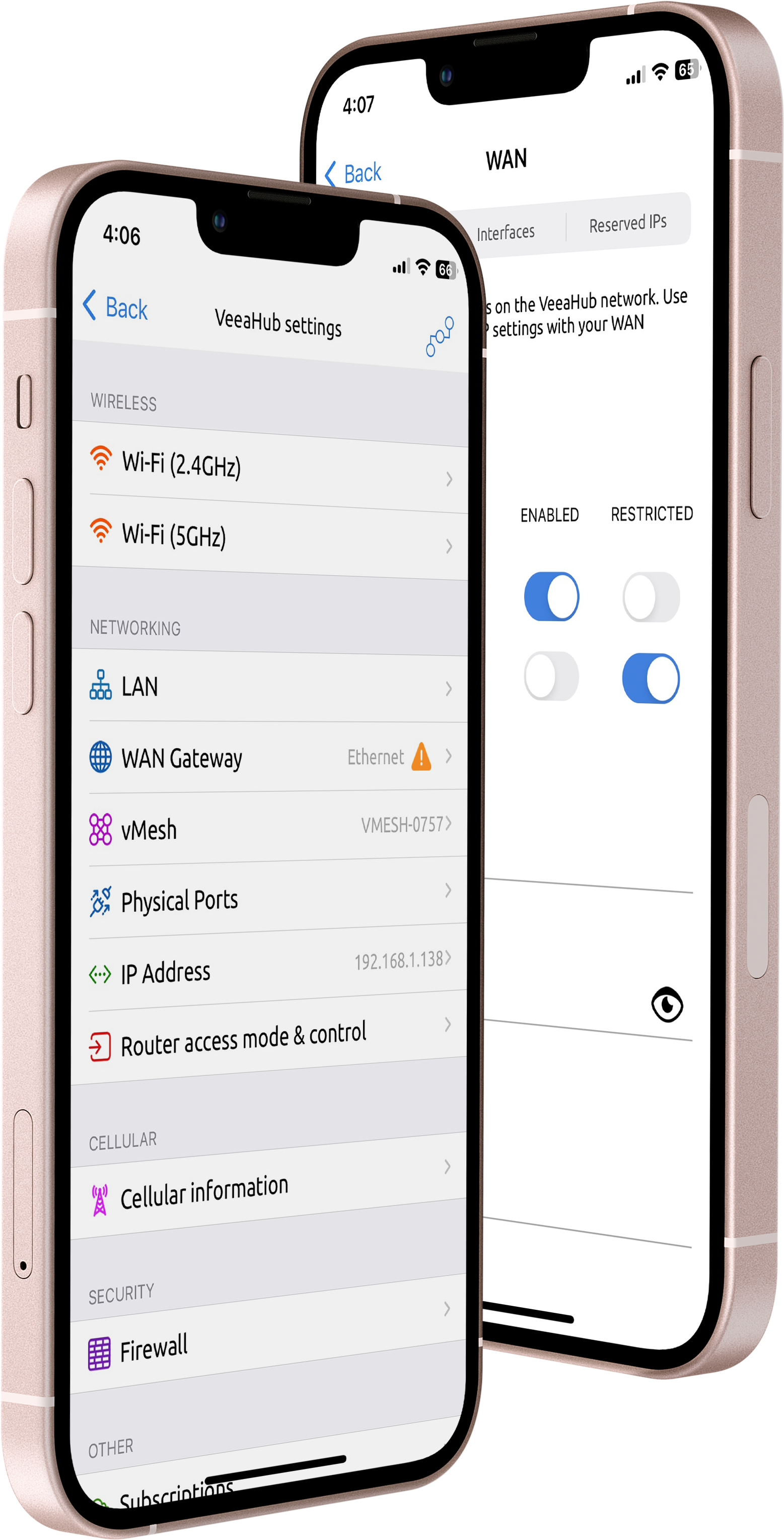
VeeaHub Manager
This mobile application, available for iOS and Android, simplifies VeeaHub registration and mesh configuration. It offers convenient diagnostics and local control, integrating your VeeaHubs seamlessly into the Control Center for efficient monitoring and management.
Connectivity
vMesh
vMesh technology redefines how nodes communicate within a network, using both wired and wireless connections. Its unique feature is the cooperative data distribution among all nodes, enhancing network reliability and efficiency. With the ability for each node to self-configure, vMesh dynamically distributes workloads, ensuring fault tolerance and reducing maintenance costs.
vBus
vBus serves as a robust hardware abstraction layer, streamlining the integration and communication of devices within the mesh network. vBus API, available in multiple languages, abstracts complexities of mesh networking and device discovery, facilitating easy configuration of edge applications.
Security
Building trust - from the ground up.
At Veea, security is paramount. Our 'Chain of Trust' architecture is meticulously designed to safeguard every layer of the Veea Edge Platform, from hardware to software. It ensures that only authenticated and trusted components operate on the VeeaHubs.
Resources
Stay Up To Date
Subscribe to our newsletter
Get the latest in edge development right into your mailbox, monthly.


